WordPress, the popular content management system (CMS), is a frequent target for hackers due to its widespread usage and open-source nature. One common hacking tactic involves inserting malicious code into the .htaccess file, a configuration file that controls website traffic and behavior.
While removing the malicious code may initially resolve the issue, it often reappears, making it a persistent and frustrating problem.
sudo grep --include=* -rn -e "suspected" 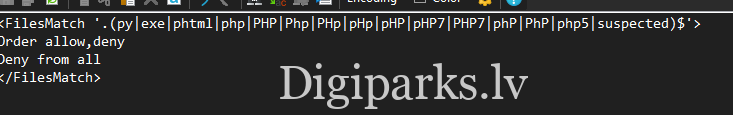
Symptoms and Detection
The presence of malicious code in the .htaccess file can lead to a variety of issues, including:
- Redirects: When a user attempts to access a legitimate page, they are instead redirected to a malicious site, often containing spam or phishing content.
- Malvertising: Invading ads or pop-ups may appear on your website, disrupting user experience and potentially compromising user security.
- Data theft: Malicious code can be used to steal sensitive user data, including login credentials and personal information.
Detection of malicious code in the .htaccess file can be challenging due to its inconspicuous nature. However, some telltale signs include:
- Unexpected redirects: If users are consistently redirected to unfamiliar or suspicious websites, it may indicate .htaccess tampering.
- Unfamiliar code snippets: Checking the .htaccess file for unfamiliar code or unusual directives can raise red flags.
- Third-party links: A proliferation of external links or references to unknown domains suggests possible malicious code insertion.
Cleaning the Infection
When faced with a persistent .htaccess hack, thorough and cautious measures are essential to eliminate the threat and prevent future infections.
sudo grep --include=* -rn -e "error reporting(0);" 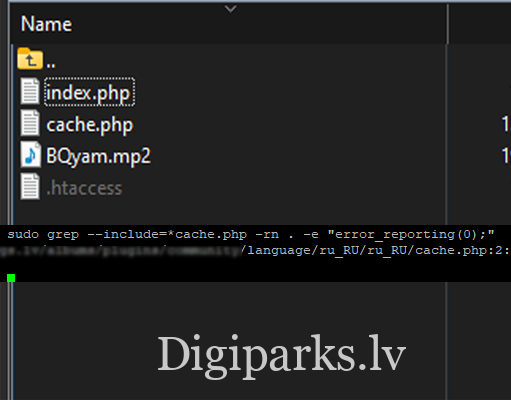
- Create a Backup: Before proceeding, make a complete backup of your WordPress files and database. This will serve as a fallback in case any further complications arise.
- Isolate the Infection: Use a reliable firewall or security plugin to block access to the infected .htaccess file. This will prevent the malicious code from executing and causing further damage.
- Manually Remove the Malicious Code: Using a text editor, open the .htaccess file and carefully search for any suspicious code or redirects. Delete any unauthorized code or directives.
- Check for Rootkits: Rootkits are malware that hide their presence within the operating system, often making it difficult to detect and remove. Use a dedicated rootkit scanner to thoroughly examine your server.
- Reinforce Security: Update your WordPress core, plugins, and themes to the latest versions. These updates often include security patches that address known vulnerabilities.
- Change Passwords: Immediately change all passwords associated with your WordPress site, including admin credentials, FTP accounts, and database access.
- Enable Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring a code from your mobile phone in addition to your password when logging in.
Opinion from an Industry Expert
“The key to preventing persistent WordPress hacks lies in implementing a comprehensive security strategy that goes beyond removing malicious code. By adopting a layered approach that includes regular updates, strong passwords, 2FA, and website monitoring, you can significantly reduce your risk of future attacks.” – Mark Johnson, IT Security Expert
Questions and Answers
Q1: What shell commands can be used to find suspicious .htaccess files?
A1: You can use the following shell commands to locate suspicious .htaccess files:
find . -type f -name '.htaccess'
Q2: How can I determine if a .htaccess file is malicious?
A2: Inspect the .htaccess file for unfamiliar code or directives that redirect traffic to unauthorized sites or inject ads. Use a security tool to scan the file for known malicious patterns.
Q3: What are some additional steps I can take to further secure my WordPress website?
A3: Implement a Content Delivery Network (CDN) to distribute your website’s content across multiple servers, reducing the impact of DDoS attacks. Utilize a web application firewall (WAF) to block malicious traffic before it reaches your website. Implement regular security audits to identify and address vulnerabilities.
